

Located in Dinajpur City, our excellent product outsourcing company provides superior full-stack development as well as offshore development center (ODC) services to meet the demand of various associations and organizations. We cover Bangladesh, Belgium, India, Portugal and Vietnam.
We not only focus on the quality and cost of our service but also advise the best solutions to meet customer's specific markets. Our incessant effort, improvement, and innovative ideas made our expert team the trusted software offshore center provider amongst our esteemed clients.
Realize all the ideas of customers using the latest technology, thereby helping them save time and costs, increase productivity to the highest level. We want to give customer the best outsourcing software development services.
To be on top 10 software development companies in Asia in 2020. Providing excellent outsourcing software development services and perfect mobile apps development and web development.
Honesty - Excellence - Experience - Cost efficiency - Support.
We provide outsourcing software development service and offshore software development center to customers. We develop innovative mobile apps and web apps to make complex things to become simple.

We simplify complicated things by designing the best mobile apps products and delivering the most innovative mobile apps and web apps to our valued customers. We have an expert team of the most senior developers with accumulated experience of over 5 years in iOS and Android applications. They ensure the innovative technology included in the producing products.

We offer fully functional and extremely practical web applications as per the industry standard and our services are fully customized that meet your business needs, objectives, and specifications.

As part of your design package, we accumulate visual and verbal brand communications guidelines. These guidelines are the major tactical statements that aid in dealing with brand strategically by all stakeholders.

Rafusoft has a proven track record of lead offshore development service, providing excellent offshore center, delivering effective software solutions to organizations worldwide. We’re a team of highly experienced and qualified software developers in Bangladesh that works in accordance with standardized methods and procedures.
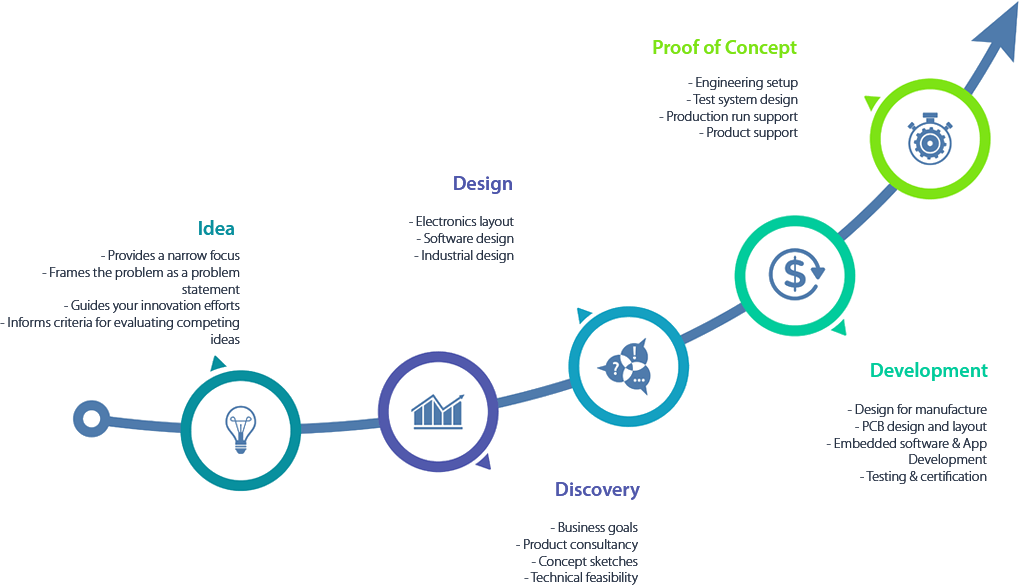
Check out the outline here that will define how we typically approach each new project in software development, including mobile apps development, and web development
➔ Clarify requirements
➔ Confirm requirements
➔ List features base on priority
➔ Create stories on JIRA
➔ Build wireframe
➔ Gather client feedback
➔ Code development
➔ Marketing review
➔ Quality Assurance
➔ Deploy apps
➔ Fixing bugs
➔ Maintain apps

Web Development
App Development

Customers

Satisfaction
Years of Trust
Projects
Subscriber
Happy Clients
It takes more than a team to realise a game changing idea, it's domain expertise and that's what we possess.
We believe in client satisfaction and we deliver projects that can successfully meet or exceed the prospects of the stakeholders.